Overview
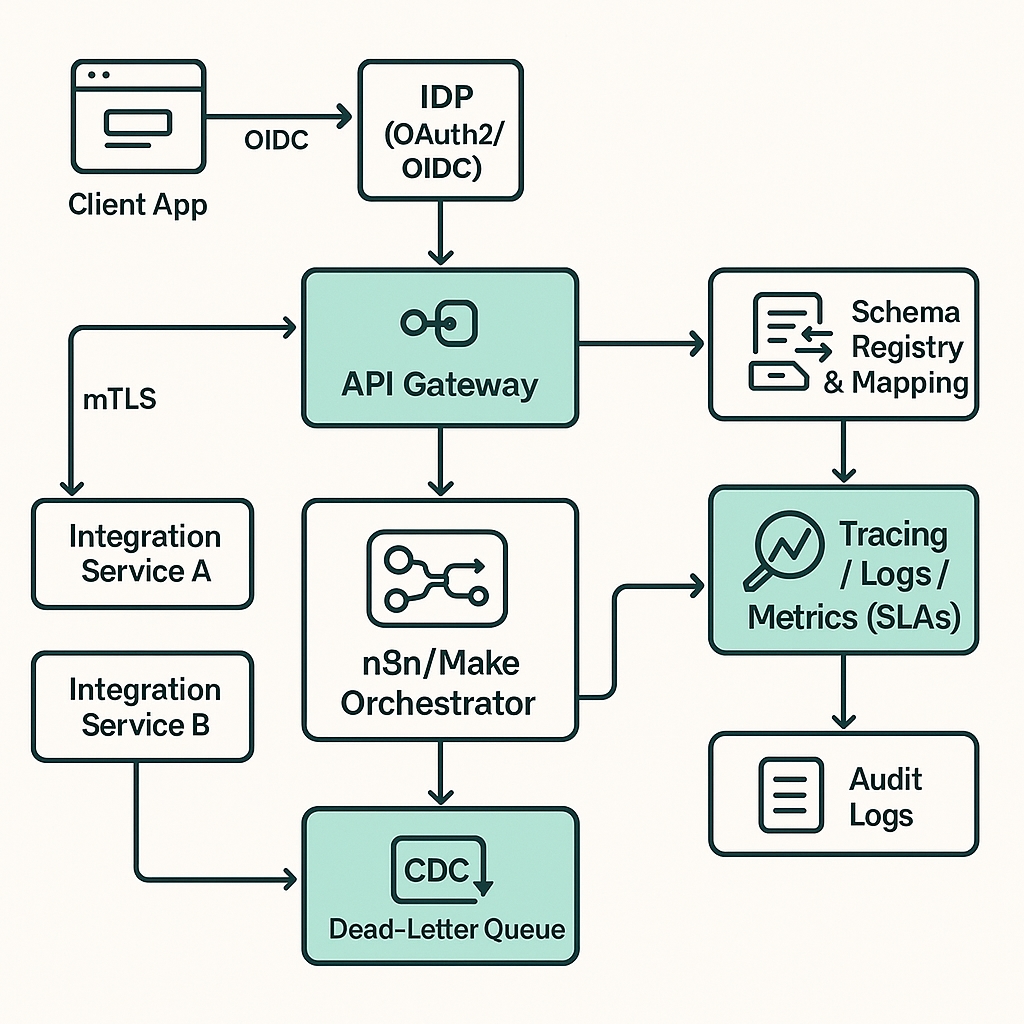
We deliver API-first, event-driven integrations across ERP/CRM/e-commerce/analytics. Patterns include sync/async messaging, ETL/ELT, and webhooks/queues. Designs are auditable, secure (OAuth2/mTLS), and observable (tracing & SLAs).
- Architecture: OpenAPI/AsyncAPI contracts, idempotency, retry & dead-letter queues.
- iPaaS & Orchestration: n8n/Make, Logic Apps, serverless workers, schedulers.
- Data: mapping & validation, schema registry, CDC, deduplication.
- Security: OAuth2/OIDC, mTLS, secrets management, audit logs.
Policy: Advisory-only; no offensive activity. Implementation by client teams or certified partners under our governance.
Our Expertise
- 🔗 API Design & Governance — OpenAPI/AsyncAPI, versioning, linting, developer portals.
- 🧩 iPaaS & Orchestration — n8n/Make, Logic Apps, queues/webhooks, cron/schedulers.
- 📦 ERP/CRM/e-Commerce — SAP/Dynamics/Netsuite; Shopify/Woo; M365/Slack/Teams.
- 📨 Messaging — Kafka/Rabbit/Service Bus; pub-sub, saga & outbox patterns.
- 🗂️ Data Pipelines — ETL/ELT, CDC, validation & enrichment, schema registry.
- 🛡️ Security & Compliance — OAuth2/OIDC, mTLS, KMS/Key Vault, auditability.
What We Do
- Discovery & contracts: system inventory, data flows, API specs & SLAs.
- Build & orchestrate: connectors, transformations, retries/idempotency.
- Secure & observe: secrets, RBAC, tracing/logs/metrics, error budgets.
- Operate & optimize: throughput/cost tuning, dashboards, runbooks.
Sample KPIs
- Integration success rate: ≥ 99.5%
- End-to-end latency (P95): < 5s
- Duplicate events: < 0.1%
- Incident MTTR: ≤ 1h
- Cost per 1k transactions: −30% in 6 months
Packages
- Starter (3–4 weeks): Integration map, target contracts, quick wins, 90-day plan.
- Growth (5–8 weeks): iPaaS setup, 2–4 flows in prod, observability baseline, runbooks.
- Enterprise (8–12+ weeks): Event-driven backbone, policy-as-code, DR/HA drills, compliance artefacts.
Method
- Discover: systems, contracts, risks.
- Design: patterns, schemas, SLAs.
- Pilot: low-risk slice with rollback.
- Implement: flows, security, observability.
- Handover: docs, training, support rhythm.
Deliverables
- Architecture & API Specs: OpenAPI/AsyncAPI, examples, mocks.
- Integration Flows: orchestrations with retries/idempotency & DLQs.
- Data Maps & Validation: schemas, contracts, test cases.
- Observability Pack: tracing/logs/metrics dashboards, alerts.
- Security & Compliance: secrets/KMS, RBAC, audit logs, hardening report.
- Runbooks: incident/change, key/cert lifecycle, DR/BCP.
Engagement Models
- Advisory-only. Implementation by client teams or certified partners; we provide design, governance, and QA.
- Vendor-neutral. No resale, no commissions, conflict-free.
- Defensive-only. No offensive testing or data exfiltration tooling.
Compliance & Client Acceptance
- GDPR/DPA-first: data minimization, least privilege, NDA with staff/partners.
- Sanctions/KYC: screened against EU/UK/US sanctions; embargoed parties refused.
- Off-limits: No offensive testing/automation, exploit development, or tool resale.
- Terms: Contracted service terms & liability limits under local law.
FAQ
- How do you avoid duplicates? Idempotent keys, outbox pattern, DLQs.
- Which stack? We are vendor-neutral; we pick tools by use-case, SLA and TCO.
- Runtime location? Customer’s cloud/VPC/VNet; secrets in KMS/Key Vault.
- Security model? OAuth2/OIDC, mTLS, RBAC, audit trails.
Ready to Move?
Share your context (goals, constraints, timelines) and we’ll recommend the right package or a tailored plan.
- Book a Discovery Call ·
- info@nemeris.com · +90 530 990 6218
- Policies (defensive-only, vendor-neutral)
We process only the details you share to respond to your inquiry. See Policies for privacy and data handling.